Innovative technique to curtail illegal copying of digital media
In today's digital world it can be challenging to prevent photos, videos and books from being illegally copied and distributed. A new light-based technique is making it more practical to create secure, invisible watermarks that can be used to detect and prosecute counterfeiting.
"In our research, we use a complex pattern of light, or diffraction pattern, as a unique watermark," said Yishi Shi, from the University of Chinese Academy of Sciences, China. "The invisible watermark is embedded into the content we are trying to protect. Imperceptibility is one of the most significant advantages of optical watermarking."
In The Optical Society's journal Optics Express, Shi and colleagues report a new approach that encodes the optical watermark in a single step. The new technique is faster and uses a less complex optical setup than other optical watermarking approaches previously pursued. The new technique can also be used to optically encrypt data or to hide information within images.
Practical watermarking
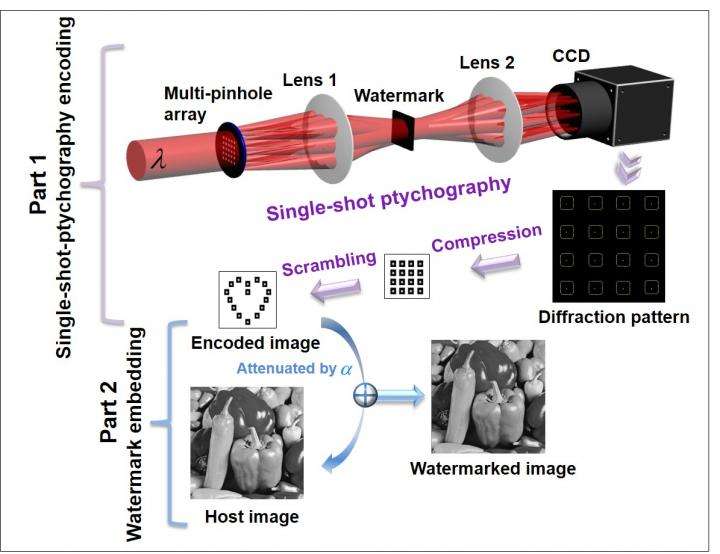
The new method is based on a technique called single-shot ptychography encoding (SPE) that uses multiple partially-overlapping beams of light to generate a diffraction pattern from a complex object. Unlike other methods, SPE can encode the optical watermark in a single exposure with no mechanical scanning. SPE is also less prone to error than other methods and uses a simpler optical setup.
In addition to conducting numerical simulations to test their method, the researchers carried out an optical experiment showing the usefulness of SPE. "Most methods for optical watermarking have only been demonstrated with simulations," said Shi. "Our experiment shows that our method is suitable for practical optical watermarking."
For the optical experiment, the researchers used SPE to create a complex watermark consisting of a diffraction pattern of multiple tiny spots. Prior to embedding the watermark into a host image, they used computer processing to remove any repeated data and to scramble the diffraction pattern, making it easier to embed the watermark and further improving its security. The spot size can be reduced to smaller than 10 microns, which helps prevent degradation of the host image.
Once a watermark is embedded into digital media, there are multiple ways to detect it to check for authenticity. If someone knows an optical watermark is present, it can be detected by subtracting the host image from the watermarked image and then using a special security key and extraction algorithm. For cases where the presence of a watermark is unknown, the watermark could be extracted using existing algorithm-based detection methods.
Upping the complexity
The researchers are now working to apply SPE to dynamic watermarking, which creates watermarks from objects that change quickly. For example, the variations that occur within a biological cell could be recorded and used to create a special watermark. They also plan to use SPE for multi-image watermarking and even 3D watermarking, while also working to further enhance the imaging quality of single-shot ptychography.
More information: WenHui Xu, HongFeng Xu, Yong Luo, Tuo Li, and Yishi Shi, "Optical watermarking based on single-shot-ptychography encoding," Opt. Express 24, 27922-27936 (2016). DOI: 10.1364/OE.24.027922
Journal information: Optics Express
Provided by Optical Society of America