Computer scientists' anti-spyware app surpasses one million downloads
"We considered such an app necessary. But we all were surprised by its actual success", explains Michael Backes, professor for Information Security and Cryptography at Saarland University and scientific director at the Center for IT-Security, Privacy and Accountability (CISPA). Last July, his spin-off Backes SRT provided the app as a free download. With "SRT Appguard" users can supervise apps they have already installed on the operating system Android and control their access permissions on resources like contact information and internet connection at any time. They do not have to be root to do this. "That is exactly what has not been possible with Android apps so far", declares Backes.
The facilities of SRT Appguard quickly attracted a lot of users. The download rate at the software registers of the German IT-portals "heise.de" and "chip.de" increased continually. In just six months 91,536 users downloaded the mini program and pushed it to 11th place in the category "Top 100 most popular apps in 2012". "If we add the balance of chip.de to the download numbers of our corporation website, we can see, that SRT Appguard has been downloaded over a million times by now", says Backes. In the meantime, the counter on chip.de stood at 178,272 and 93 percent of the users gave the app a thumbs up. The app was also available on the DVD that was included in around 230,000 copies of this year's January issue of the magazine.
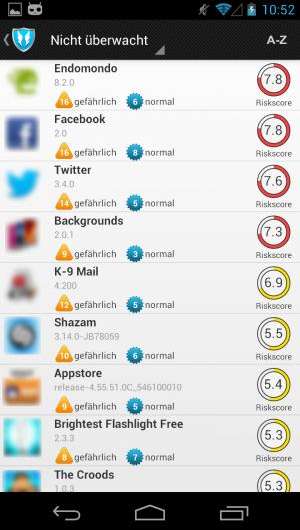
Now, the new corporation offers a commercial version of the app. Since the beginning of April, "SRT Appguard Pro" can be found on the web portal "Google Play" for 3,99 Euros. Soon, the computer scientists in Saarbrücken will offer their app for the same price at "Samsung Apps". The South Korean company has invited Backes SRT to do so. One of the major assets of the commercial version over the free version is its improvement regarding ease-of-use, and the ability to support updates of monitored apps. A "risk score" graphically presents the danger of the current right-configuration for each app. "On this way we make it easier for the users to assess the potential danger on their smartphones and tablet PCs", explains Philipp von Styp-Rekowsky, chief technical officer of Backes SRT and doctoral candidate at Professor Backes' department.
He is assured that the importance of this will increase in the future. Furthermore, the app runs significantly faster and works on every Android version starting from version 2.3. The updating process of the installed apps also works. Within the first version, this wasn't possible.
More information: www.srt-appguard.com/de/
Provided by University Saarland