January 6, 2012 report
Apple patent sends password secrets to adapters
(PhysOrg.com) -- First-time computer users in the early days, pre-hacking security traumas, were confronted with a new life requirement: creating and remembering system passwords. Not too easy, users were warned, to protect their privacy against snooping brothers and sisters, but not too tough, so they can easily remember it all times. This is no longer good advice, and Apple has filed a patent that says, no, make your password as tough as you want.
The patent filed by Apple seeks to help users recover their password information with use of a charger peripheral that doubles as the user’s security key for password recovery.
Apple says in the patent application, dated July 2010 and made public this month, that too often users choose to make their passwords simple, which just makes the work of thieves all that easier. Instead, Apple is suggesting that a user’s MacBook or smartphone or any iOS device password recovery information could be stored inside its charging adapter.
The idea is to shift the security information to the adapter, in the event that the user’s laptop or smartphone or tablet is stolen or otherwise missing. In so doing, the user can make it tough for thieves because the user can feel free to construct more complex password strings.
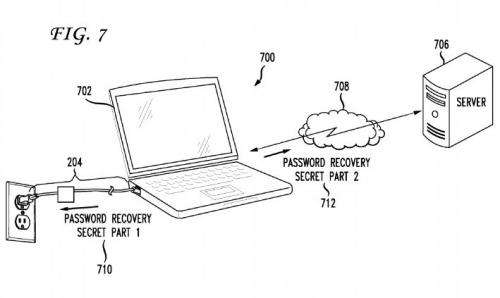
Once the user plugs in the peripheral, the recovery process for password retrieval and display is done.The patent application is titled, “System and Method for Storing a Password Recovery Secret,” and the inventor is named as Guy Tribble, of Hillsborough, California. Apple is proposing that a small memory module built into the unit holds the password or recovery question.
For users really concerned about security complex enough to thwart thieves skilled in working out passwords, Apple suggests the user might want to use multiple peripherals as an alternative scenario, where the adapter could hold part of the information and the other could reside elsewhere, as on some remote network server.
The patent application’s idea seems useful obviously in instances where one is travelling with the laptop or other mobile computing device but not the charger. Apple is assuming the user taking advantage of this password-retrieval approach leaves the charging device behind, at home or in some desk or locker, before going out on the road.
While many reactions have been favorable to the patent idea, others note that the assumption may be too easily drawn. Some laptop users always carry their chargers with them because of limited battery life, though tablets and smartphones last a long time. A heist that includes both charger and computer places the user out of luck, say some detractors, who also note that cyber thieves eventually will figure out password information on the charger too. Detractors also note that as soon as the time would come for such a device to go commercial, thieves would start seeking out such chargers as worthy for stealing.
More information: Patent text online: www.pat2pdf.org/patents/pat20120005747.pdf
© 2011 PhysOrg.com