Pathogens attack plants like hackers, so my lab thinks about crop protection like cybersecurity

Plants feed us. Without them we're goners. Through thousands of years of genetic modification by selective breeding, humans have developed the crops that keep us alive. We have large kernels of grains, plump fruits and nutritious, toxin-free vegetables. These forms would never be found in nature, but were bred by people to keep us healthy and happy.
Unfortunately, microbes find our wonderfully productive food plants just as delicious as we do. These plant pathogens cause diseases that have changed world history and still affect us today.
These pathogens are plant hackers. Just like computer hackers, they're specialized infiltrators, adept in stealth and disruption. The methods are the same, too: shut down defenses and access the target's resources. Once they're in, plant pathogens eat all they can and reproduce wildly. Computer hackers desire wealth or information, but the plant hackers are after our food. Up to 25 percent of crops globally are lost to diseases before they reach market.
Oomycetes on the attack
The most infamous and cunning plant hackers are the oomycetes. The Irish Potato Famine in the 1840s was caused by the oomycete Phytophthora, Greek for "plant destroyer." This biological disaster led to the emigration of millions of people to the United States, and changed both countries forever. Even today, oomycetes and the rest of the plant pathogens remain a barrier to global food security, contribute to malnutrition and cost billions of dollars in losses annually.
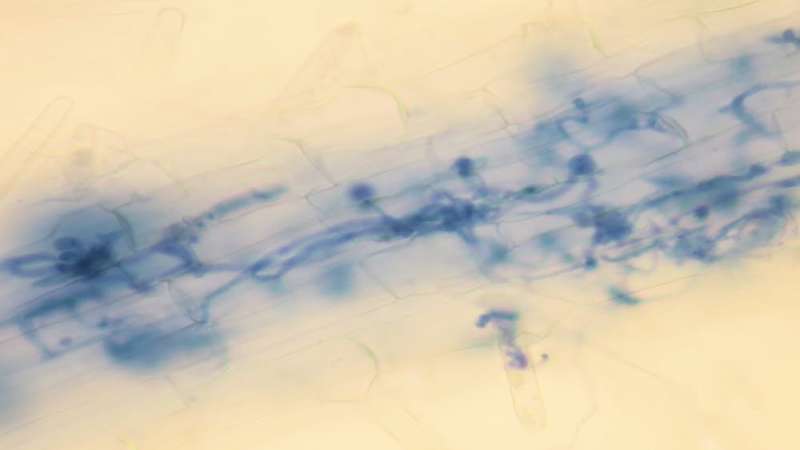
The oomycetes are a strange product of evolution. They look and behave like fungi; hence their Greek name "egg-fungus." It wasn't until the advent of gene sequencing that researchers correctly identified the oomycetes as a relative of algae, not fungi. Oomycetes start as single microscopic spores that infiltrate plant leaves or roots undetected. Once inside, they establish a perverse connection with the host plant's cells. The hackers gain access and can mess around with anything they want – from switching off the plant's security systems to breaking into stores of plant nutrients.
Evolution has given the oomycetes a repertoire of toxins and proteins that converge on hubs of the plant immune system to disable it. Plants can fight back against these attacks if they recognize oomycete-specific chemicals or the hackers' toxins. But detection is difficult and fleeting. The oomycetes hackers have genomes built for evolution. Core genes for metabolism and growth mutate and change at a normal pace. However, genes for toxins, and those that control infection are positioned to rearrange, combine or be turned off after a single generation. These new forms evolve so quickly that they baffle the slow-to-change plant immune system. This "two-speed genome" means the oomycetes always have a leg up on plant immune detection. When farmers use genetically identical crops year-to-year, oomycetes don't take long to evolve around plants' defenses.
So how do researchers and growers stop the plant hackers and help crops? Despite the cost and drawbacks, pesticide has been an important tool to control plant disease.
Farmers try to use minimum effective amounts of fungicide, which helps lower the chance oomycetes will develop resistance. For instance, the Cucurbit Downy Mildew Forecast Service in Georgia combines reports of disease with weather forecasts to predict the likely path of disease spread. This allows growers to minimize sprays by sticking to high risk periods.
But it would be nice to have other weapons in the arsenal to fight off these plant hackers.
Getting rid of exploitable loopholes
In the McDowell lab where I research here at Virginia Tech, we look for new ways to combat oomycete diseases.
Computer hackers rely on exploiting flaws in code to access systems and take what they want. Oomycetes work the same way, using their host to achieve their ends. For instance, plant diseases activate natural plant pumps to supply sugar for their own growth. Some oomycetes have lost the capacity to produce critical nutrients, meaning they rely on their plant host to do it for them. Without the plant host susceptibilities, the pathogen would starve before the plant got sick.
My colleagues and I study oomycete disease in the model plant Arabidopsis, more commonly called thale cress. This weed is only grown in laboratories, but, like lab mice for humans, provides a tool to understand what goes on in our fields, orchards and gardens.
We focus on the relationships between plants and pathogens, looking for other ways oomycetes exploit their hosts. If we can identify the mechanisms of plant cell machinery that a pathogen requires to cause disease, we can breed or engineer plants to change, turn off or get rid of those vulnerabilities.

We test plants that have been genetically manipulated to turn off individual genes related to nutrient uptake, transport, storage and regulation. We infect these modified plants and look for any that are more resistant than their normal relatives.
Often the removal of a gene is detrimental to the plant and the disease suffers as well. But occasionally we find a test plant that, despite its inactive gene, does just fine – and is less susceptible to the disease. Potentially, those plants lack a key component the pathogen requires to survive and grow. Finding those susceptibility genes and closing those exploitable holes in plant defense is my goal.
Looking forward, there is hope that research can diminish the impact of plant diseases. Like a computer, no plant defense system is perfect. However, if loopholes can be closed, hackers will have a much tougher time accessing what they're after. Both breeding and genetic engineering provide paths to close those loopholes that may also exist in the vegetable crops that are most affected by plant hacking.
Even if everyone on Earth had enough to eat, a growing population, increased demand for meat, and a need for more fresh produce necessitates growing more food. This can either come from more farmland or more efficient farms. Strategies that employ limited pesticide use along with plants that are more resilient to the pathogen hackers could make the farms we have more productive.
Provided by The Conversation
This article was originally published on The Conversation. Read the original article.![]()



















