Mobile quarantine station for malicious Android apps
The attacks were perfidious: In February this year, the Czech IT security company Avast declared that it had identified several malicious game apps for mobile phones in the Google Play Store – ones that would only become criminally active on the device after several weeks. Then the affected smartphones or tablet computers would suddenly take minutes, instead of seconds, to display all the usual settings in proper colors. Or a message would appear when unlocking the device, claiming that the memory was infected or full of pornographic data. Anyone following the instructions given there would be redirected to suspicious sites, which make users download even more malicious programs (malware).
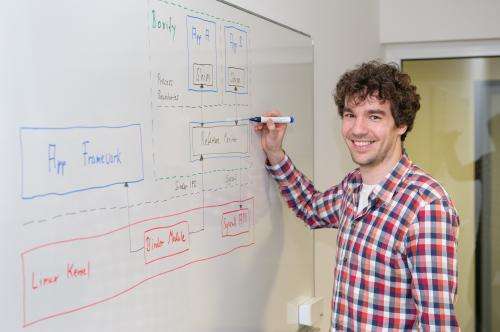
"Regardless of whether the application is malicious or not, recreational games that you just want to play around with can be downloaded without hesitation using our method," says Philipp von Styp-Rekowsky. The computer scientist is a doctoral candidate at the Saarland University Graduate School for Computer Science, and also a researcher at the Center for IT-Security, Privacy and Accountability (CISPA), one of three security research centers in Germany that are specifically funded by the German Federal Ministry of Education and Research, BMBF.
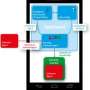
What von Styp-Rekowsky developed for mobile devices with an Android operating system, already exists for operating systems on personal computers – the keywords are "Application Virtualization" or "Sandboxing". This is what software experts call those specially insulated areas of a program where its computations can have no effect whatsoever on its environment. Accordingly, von Styp-Rekowsky designed an app that acts as a kind of "quarantine station", isolating suspicious-looking apps installed on devices like smartphones and tablet computers.
"This has some significant advantages compared to previous methods," says von Styp-Rekowsky. "So far, this kind of controlled execution of oversight when executing suspicious apps could only be achieved either by interfering with the operating system, or by modifying the executable code of the app. In the first case, users would need to install a special version of the operating system, but in the second case, as soon as you change the code, you are no longer on firm legal ground, and will also lose the application data as well as the automatic update function." However, both these methods would not only be overwhelming to less experienced users, in the worst case, they could even make the device inoperative.
Von Styp-Rekowsky's sandbox approach works around these difficulties. "The installation process for apps is just the same as before. Users only need to make sure that it happens inside the sandbox," the researcher says. Moreover, his system not only serves as a protection against data theft, it is also useful for business clients with issues related to the trend to "bring your own device": It is becoming increasingly common that employees use their personal devices for official duties. In terms of IT security and legal certainty, this is certainly a major challenge for employers. "With the help of our app, a company could set up a segment of the employee's device in such a way that it is limited to work-related activities, allowing better protection of the interests of both the employer and the owner of the device," von Styp-Rekowsky explains. The app is still a research prototype presently, but will be developed into a marketable application in the next few months.
Provided by Saarland University