UK codebreakers stumped by WWII pigeon message
British intelligence officials are baffled by a secret World War II message that was discovered on the leg of a dead pigeon, they admitted on Friday.
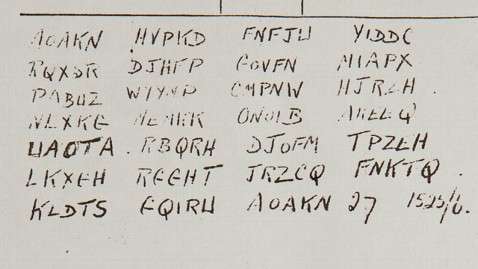
The message, consisting of 27 hand-written blocks of five letters, was attached to a pigeon skeleton that was found by retired probation officer David Martin when he was renovating his house in Surrey, southeast England.
Martin handed the piece of paper to experts at intelligence agency GCHQ at the start of November, and they have been scratching their heads ever since.
Codebreakers said the message, which did not include a date, was impossible to crack without its codebook.
Written on a small sheet of paper headed "Pigeon Service", the code was found in a small red canister and listed the sender as "Sjt W Stot". The recipient is named as "X02".
A GCHQ spokesman said: "Although it is disappointing that we cannot yet read the message brought back by a brave carrier pigeon, it is a tribute to the skills of the wartime code-makers that, despite working under severe pressure, they devised a code that was indecipherable both then and now."
Britain used some 250,000 pigeons as military messengers during World War II.
More information: The message in full reads:
AOAKN HVPKD FNFJW YIDDC
RQXSR DJHFP GOVFN MIAPX
PABUZ WYYNP CMPNW HJRZH
NLXKG MEMKK ONOIB AKEEQ
WAOTA RBQRH DJOFM TPZEH
LKXGH RGGHT JRZCQ FNKTQ
KLDTS FQIRW AOAKN 27 1525/6
(c) 2012 AFP