Keeping an eye on intruders
Electronic fingerprinting, iris scans, and signature recognition software are all becoming commonplace biometrics for user authentication and security. However, they all suffer from one major drawback - they can be spoofed by a sufficiently sophisticated intruder. Writing in the International Journal of Biometrics, Japanese researchers describe a new approach based on a person's reflexes that could never be copied, forged, or spoofed.
Masakatsu Nishigaki and Daisuke Arai of Shizuoka University, Japan, explain how the use of biometrics for user authentication is becoming increasingly widespread. "Biometrics makes it possible to authenticate a person accurately," they say.
A digital fingerprint pad hooked up to a computer, for instance, can provide access to online resources only to specific individuals based on their unique fingerprint. Signature recognition allows a person to receive information or goods only if their signature matches the imprint held in a database. Iris scanning technology identifies a person and allows them access to a building only if they have authorization. There are several other biometrics in development, based on the pattern of blood vessels in the retina or skin and other such phenomena.
"However, biometric information can easily be leaked or copied," the researchers point out. "It is therefore desirable to devise biometric authentication that does not require biometric information to be kept secret."
To this end, the team has turned to one phenomenon that cannot be spoofed - a person's unique reflex responses. They point out that even if a person's pattern of reflex characteristics were revealed to a malicious third-party, they would not be able to replicate them adequately to impersonate the authorized individual. Reflexes by their very nature are beyond conscious control.
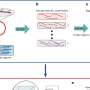
Nishigaki and Arai have turned to blind spot position and the so-called saccade response for their biometric. The blind spot, or scotoma, is a fixed region on the retina of the eye where the optic nerve bundle and blood vessels pass from the eyeball into the brain and so no image can be produced here. The position of the blind spot can be determined relative to the direction of gaze. Saccade response is the repeated, tiny, left-to-right movements made when our eyes track something moving right to left, and vice versa.
If physiological biometric information, such as blind spot, were used alone, Nishigaki adds, the possibility remains that an impostor could use surgery or an ingenious contact lens to change the shape of their own eyeball, and be successful in impersonating someone else. Blind spot alone would be no more sophisticated than iris recognition.
By using the blind spot position as a trigger to induce saccades, user authentication can be done by displaying a target within and outside the person's blind spot and using eye tracking technology to measure the reflex time taken until eye movements occur. Each pattern of responses will be unique to the individual.
An authentication system of this type could not be spoofed even if the attacker were to use sophisticated materials, equipment, or even surgery. "Our method transforms differences in physiological biometric information (blind spot) into "differences in human reflexes (saccade) and uses it for authentication," Nishigaki says.
The team has also now published a second version of the reflex-based user authentication that uses blind spot position and pupil contraction and a third version that uses vergence, or crossing, eye movements. These papers have been published in the scientific literature in Japan.
Source: Inderscience Publishers