Software Tool Plugs Security Leaks
Often when you make an Internet transaction, symbols on the Web page assure you that your transaction will be secure and that private information about you, such as passwords, bank account or credit card numbers, will not be intercepted by a third party.
Such assurances mean safe passage along the information highway. But is your private information secure after it enters a merchant's computer?
Not necessarily, says a University of Illinois at Chicago computer-security expert who is developing a software tool that will help keep private information from falling under prying eyes.
"There are many ways software can leak information, and often programmers are clueless about how to prevent it," said V.N. Venkatakrishnan, assistant professor of computer science and co-director of UIC's Center for Research and Instruction in Technologies for Electronic Security.
"Programmers need tools and techniques to write good code that safeguards private data," he said. "It is important to address end-user privacy concerns during software development."
The problem focuses on the massive number of computer programs written in C, the language most widely used for building systems software for applications such as mail agents, calendars and web browsers.
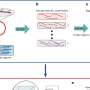
Building on previous research findings, Venkatakrishnan has developed a software tool to break up private, protected data-entering programs written in C, separating it from information that is open to public access, such as via an Internet link. The tool automatically identifies what Venkatakrishnan calls the program's public and private zones, monitoring the program while running, checking the information flow almost like a gatekeeper dividing attention between these two zones.
"Taken together, the public and private zones replace the original functionality of the program," he said. "It enables you to enforce different policies on these zones. For instance, the public zone is not allowed to read sensitive data, and the private zone is not allowed network access, which addresses end-user privacy concerns."
Venkatakrishnan has already developed a prototype tool and has successfully tested it on medium-scale software programs. He just received a two-year, $250,000 single-investigator grant from the National Science Foundation to create a way to scale-up the tool for use on large-scale programs, such as mail readers and Web browsers.
The tool will be easy for programmers to use, and applicable to a wide range of programs, Venkatakrishnan said. He expects to have it tested and ready for public release within two years.
"The prototype is there. It will be fairly easy for us to build on it."
Source: University of Illinois at Chicago