China's quantum satellite could make data breaches a thing of the past

China recently launched a satellite into orbit with a unique feature: it has the ability to send information securely, not with mathematical encryption but by using the fundamental laws of physics. China will be the first country to achieve this feat, and it marks a milestone in the development of quantum technologies.
The next revolution in technology promises to embrace fundamental laws of physics to enable devices to perform operations that are beyond the bounds of current electronics. The potential of quantum computers to tackle some of the most complex mathematical problems is very exciting. But information security provided by quantum communications could be just as important.
Our society relies heavily on digital communications. In the last three years, we sent more information through the internet than had been communicated in the whole of human history before this period. A large proportion of this data is sensitive and we often want to keep it from prying eyes. But how can we trust communications over the internet when it relies on data travelling down chains of potentially unknown computers? Taking a place on one of these chains and snooping on the data as it passes by seems all too easy.
The current solution to this communications challenge is to use complex mathematics in a series of algorithms known as public key cryptography. But the increasing power of computers and ingenuity of hackers is opening up more and more cracks in this mathematical armour. An ideal solution to this problem would provide provable information security, guaranteeing the safety of our personal information. This is where quantum physics steps in.
Laser technology
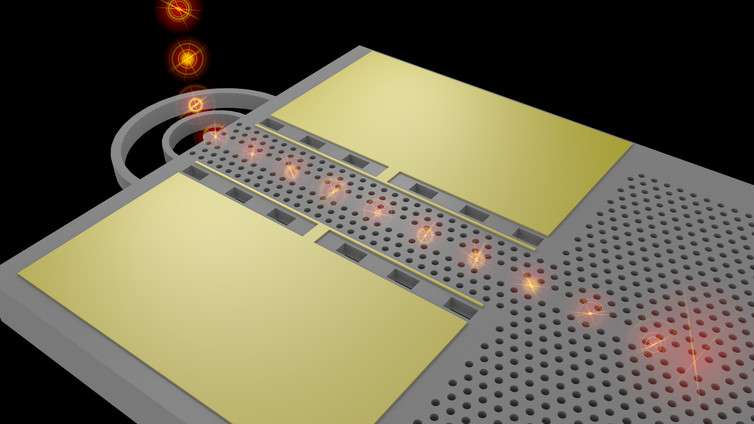
The technology on board China's new satellite is simple in design and almost magical in operation. A special crystal divides a laser into two beams that are then directed to independent receiving stations on Earth. These beams share a property of quantum mechanics known as entanglement, which links them together even when they are far apart. Actions performed on one beam will also affect the other beam.
The trick to secure communications lies in this odd relationship between the two beams. The link is used to send random data from one receiving station to the other. This data can be collected and used, essentially as a complex password, to encrypt data sent over a public channel such as the internet. This method of communications was invented by a famous quantum physicist, Artur Ekert. Crucially, it is proven to be secure against eavesdropping and hacking. Quantum physics cannot be cheated, tricked or reverse engineered, unlike the complex mathematics of conventional cryptography.
China's new satellite is an important step towards truly secure communications, as it allows quantum data to be sent over extreme distances between any two locations. At the moment, with just one satellite, the technology's capabilities are limited, but it is easy to see how it will scale up as more satellites are launched and performance improves.
The next important piece to this puzzle lies at the opposite end of the length scale. The majority of communications flow along chains, and the strength of a chain is only as good as its weakest link. For practical quantum communications we need devices integrated into our computers and smartphones that exchange data in a similar way to the quantum satellite. These devices are thankfully just around the corner. In a few years we may look back on digital eavesdropping and massive information breaches from databases as a problem buried in the past.
Source: The Conversation
This article was originally published on The Conversation. Read the original article.
![]()