October 10, 2012 report
Distributed Credential Protection: Trying to beat the hackers and protect our passwords
(Phys.org)—Recent breaches at LinkedIn and Yahoo have heightened the public's concern about password protection. At LinkedIn, millions of user passwords were found and publicly posted. And at Yahoo, hackers broke into a server and stole passwords which were then used to breach other accounts with the same passwords in use. In response, computer security company RSA has developed a technique that it claims can prevent hackers from gaining access to user passwords on servers.
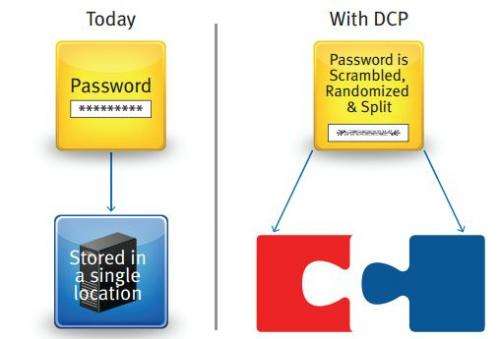
The idea is based on a technique called threshold cryptography, where data is taken apart, encrypted, and stored in separate pieces on different servers. Until now, the practice has primarily been restricted to use by sites that require very high security, such as those that deal with financial data. RSA is proposing a similar technique it calls Distributed Credential Protection (DCP) for use by commercial websites to protect user passwords.
With DCP, user passwords are split into two strings of data with each piece saved to a separate server. When a user logs into the system, the password is split into two separate strings, each of which is sent to one of the password servers. There, it is joined, in random fashion, with the half of the password stored on that server to build a new string. To verify the password, the two strings on each server are compared to one another. With this scheme, a hacker would be forced to access both servers in order to gain access to user passwords. And, this process could be further complicated if each server were to run a different operating system. RSA says that to make things even more difficult for hackers, systems administrators could periodically refresh the random half of the strings, which would force those seeking entry to crack both servers within a shorter time frame.
Using DCP would make stealing passwords from website servers significantly more difficult; however, it wouldn't prevent passwords from being stolen directly via malware on users' computers. To address that threat, RSA recommends that users use different passwords for their various accounts in order to limit the degree of damage that could potentially result if one of them is stolen.
More information: www.emc.com/security/rsa-distr … ntial-protection.htm
© 2012 Phys.org