July 29, 2014 weblog
New type of ransomware more sophisticated and harder to defeat
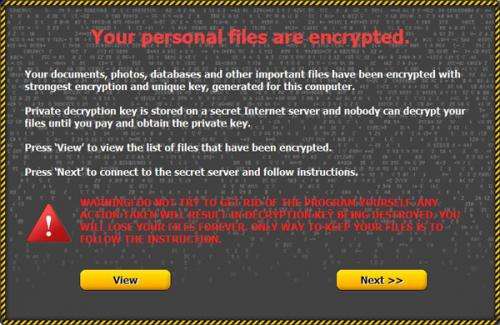
A new type of ransomware known simply as Onion, has been discovered by Russian based security firm Kaspersky Lab. To force victims to hand over money, the software encrypts stored data files and then uses Tor (anonymity network) to facilitate transfer of funds anonymously. Thus far, the ransomware appears to be restricted mostly to Windows users in Russia and other eastern European countries.
Ransomware is a relatively new development, it's not a virus, per se, but instead is software that runs without permission on a user's computer. In the past, the software would display a full screen message demanding money be sent with instructions on how to do so. The full screen message would, theoretically remain on the screen (even after rebooting) preventing any other applications from running, thus preventing the user from using their computer until they paid up. Antivirus makers quickly developed workarounds for most such ransomware, and authorities discovered the source of most of the software and blocked it from working—in the end the threat was mitigated in most places. Now it appears, its back and this time it's much more sophisticated.
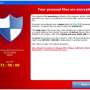
A user is typically attacked when they click on a link in a piece of junk mail. That sets in motion a series of events that leaves the victim stuck with little choice but to pay the ransom. A popup is displayed informing the user that their files have been encrypted (along with a list of files that have been encrypted) and telling them that they must pay in Bitcoins, or else the key to unlock their files will be destroyed, forever preventing the user from regaining access to them.
Using the Tor network makes it nearly impossible for authorities to track down the people behind the malware—also the makers have used an unorthodox encryption scheme that disallows decryption even if the communications traffic is intercepted. Inspection of the code by researchers at Kaspersky Lab revealed the programmer was likely a native Russian speaker.
Thus far computer users impacted by the ransomware have been restricted to those living in Russia and several countries that were formerly part of the Soviet Union. Experts predict it will only be a matter of time, however, before it spreads, thus efforts are underway to subvert the threat and to find those responsible for it. In the meantime, security experts are advising computer users to back up their files onto removable media.
© 2014 Tech Xplore