Remote control for the office desk
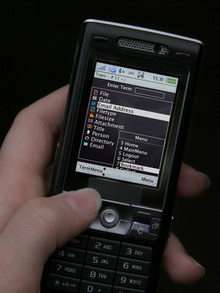
Business travelers will soon be able to access all the information on their own computers from a cell phone. A new software program makes it possible to swiftly find documents, appointments and e-mails at any time and to forward them immediately – all from a cell phone.
You can do a great many things with a cell phone – call up e-mails,
display appointments, and download documents from the Internet over a mobile connection while on the road. However, this mobile data retrieval system still leaves much to be desired. Before very long, a jumble of appointments, e-mails and documents has piled up.
Research scientists at the Fraunhofer Institute for Secure Information Technology SIT in Darmstadt want to put an end to this chaos. In a project entitled MIDMAY, they have transformed the cell phone into a kind of remote control for the computer workstation, enabling travelers to access all information on their own computers while away. It is possible to locate documents on the remote computer, attach them to e-mails and send them directly to any desired address.
A few keystrokes are all that’s required to send the data on its way. Whereas in the past, when you wanted to send an important document to someone you had met at a conference, you could only promise to send it the next day, it will soon be possible to transfer the document via MIDMAY while the conference is still in progress.
At the heart of the smart remote-control system is a server, the home base, which accesses the data stored on the workstation. What makes this system different is the way in which it cleverly interlinks the wealth of different information, making it possible to search for information on your own computer via various search paths while away from the office.
If you have forgotten who has already been sent a certain attachment, you can extend your search by entering the date, for instance. Thanks to a link with the calendar data, the number of mails can thus be limited and the required message is easily found. "MIDMAY not only permits rapid access to information, though," says MIDMAY project manager Jens Heider of the SIT. "The best thing about it is that, for the first time ever, you will be able to use your cell phone as a control center for your own digital knowledge base."
The researchers have developed not only the home base, but also a program for the cell phone that can operate reliably even in areas with no reception. "One of our main concerns was to clearly display the information on the tiny monitor and to navigate with as few keystrokes as possible," Heider adds. A first prototype will be on display at CeBIT, which takes place in Hanover from March 15 to 21.
Source: Fraunhofer-Gesellschaft