Scientists predict mobile phone viruses will pose a serious threat
(PhysOrg.com) -- If you own a computer, chances are you have experienced the aftermath of a nasty virus at some point. In contrast, there have been no major outbreaks of mobile phone viral infection, despite the fact that over 80 percent of Americans now use these devices. A team headed by Albert-Laszlo Barabasi, director of the Center for Complex Network Research at Northeastern University, set out to explain why this is true.
The researchers used calling and mobility data from over six million anonymous mobile phone users to create a comprehensive picture of the threat mobile phone viruses pose to users. The results of this study, published in the May 22 issue of Science, indicate that a highly fragmented market share has effectively hindered outbreaks thus far. Further, their work predicts that viruses will pose a serious threat once a single mobile operating system's market share grows sufficiently large. This event may not be far off, given the 150 percent annual growth rate of smart phones.
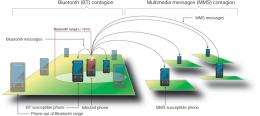
"We haven't had a problem so far because only phones with operating systems, so-called 'smart phones', are susceptible to viral infection," explained Marta Gonzalez, one of the authors of the publication. "Once a single operating system becomes common, we could potentially see outbreaks of epidemic proportion because a mobile phone virus can spread by two mechanisms: a Bluetooth virus can infect all Bluetooth-activated phones in a 10-30 meter radius, while Multimedia Messaging System (MMS) virus, like many computer viruses, spreads using the address book of the device. Not surprisingly, hybrid viruses, which can infect via both routes, pose the most significant danger."
This study builds upon earlier research by the same group, which used mobile phone data to create a predictive model of human mobility patterns. The current work used this model to simulate Bluetooth virus infection scenarios, finding that Bluetooth viruses will eventually infect all susceptible handsets, but the rate is slow, being limited by human behavioral patterns. This characteristic suggests there should be sufficient time to deploy countermeasures such as antiviral software to prevent major Bluetooth outbreaks. In contrast, spread of MMS viruses is not restricted by human behavioral patterns, however spread of these types of viruses are constrained because the number of susceptible devices is currently much smaller.
As our world becomes increasingly connected we face unprecedented challenges. Studies such as this one, categorized as computational social science, are necessary to understand group behavior and organization, assess potential threats, and develop solutions to the issues faced by our ever-changing society.
"This is what statistical analysis of complex systems is all about: finding patterns in nature," said Gonzalez. "This research is vital because it puts a huge amount of data into the service of science."
(Click here to enlarge animation)
Provided by National Sleep Foundation (news : web)
















