Tool makes scanning the internet for illegal images possible

Researchers at the University of Twente have developed a system that makes it possible to scan traffic on the Internet for illegal photographs. The system can, for example, help trace child pornography on the Internet without infringing on the privacy of Internet users. Internet service providers could use the tool to keep their network 'clean'.
The police use a standard database to detect illegal photographs, like child pornography, on equipment they seize, such as computers or USB sticks. For security reasons, the database cannot be used to scan networks such as the Internet. Were the database to end up in criminal hands, criminals could use it to make their own illegal photographs untraceable. With the system of the University of Twente, the police database can, from now on, be used to scan a network as well. This makes it possible to search for illegal photographs without the risk of the database ending up in wrong hands. Another advantage of this system is that the police can only see the number of illegal photographs to be found on the Internet; they cannot see the actual photographs. Therefore, the privacy of the owner of the photographs remains safeguarded. Despite the technical possibilities of the system, it is not yet clear what the consequences are in terms of current Dutch legislation. The researchers still want this verified from a legal point of view.
Hash values
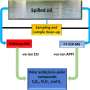
The standard police database does not contain any truly illegal photographs but only features of these photographs expressed in numbers (hash values). When the police seize equipment, such as a PC, the database is brought into action to compare the known hash values with those of the photographs on the PC. In this way, the police are able to verify whether the equipment contains any illegal photographs. The new system is a special encryption of the police database. Researcher Andreas Peter says: "You can compare it with a sort of safe, the contents of which you cannot see but in which you can place photographs. Subsequently, it is the 'safe' alone that scans the photographs and then sends a confidential report to the police. The police can open this report with a special key. The report indicates how many illegal photographs are in the safe."
With this new system, Internet service providers can also use the police database to scan their network for illegal photographs. At this time, the University of Twente is consulting with companies that are interested in starting to work with the system. A scientific article about the prototype will soon be published during ICASSP 2014, an international conference on signal processing.
Provided by University of Twente