DARPA open catalog makes agency-sponsored software and publications available to all
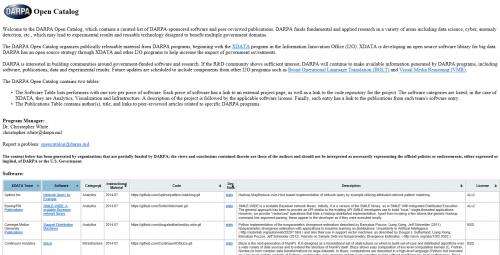
DARPA has invested in many programs that sponsor fundamental and applied research in areas of computer science, which have led to new advances in theory as well as practical software. The R&D community has asked about the availability of results, and now DARPA has responded by creating the DARPA Open Catalog, a place for organizing and sharing those results in the form of software, publications, data and experimental details.
The Catalog can be found at go.usa.gov/BDhY .
Many DoD and government research efforts and software procurements contain publicly releasable elements, including open source software. The nature of open source software lends itself to collaboration where communities of developers augment initial products, build on each other's expertise, enable transparency for performance evaluation, and identify software vulnerabilities. DARPA has an open source strategy for areas of work including big data to help increase the impact of government investments in building a flexible technology base.
"Making our open source catalog available increases the number of experts who can help quickly develop relevant software for the government," said Chris White, DARPA program manager. "Our hope is that the computer science community will test and evaluate elements of our software and afterward adopt them as either standalone offerings or as components of their products."
The initial offerings in the DARPA Open Catalog include software toolkits and peer-reviewed publications from the XDATA program in the agency's Information Innovation Office (I2O). The partially funded toolkits are designed to encourage flexible development of software that may enable users of targeted defense applications to process large volumes of data in a timely manner to meet their mission requirements.
Provided by DARPA