January 23, 2014 weblog
Hacking feat spots ghosts in Snapchat's new verification tool
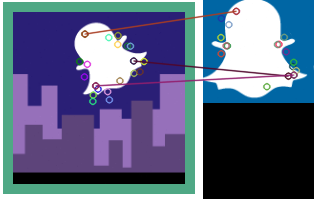
(Phys.org) —Chat service company Snapchat this week announced it was further nailing down its security with a new identification verification system, beyond fancy font-annoying CAPTCHAS, that could seal the deal in telling humans apart from information harvesters and malicious bots. With the new tool, site visitors are shown nine picture tiles, some with Snapchat's ghost mascot and some without. Users need to differentiate among the pictures, to choose the ones showing the ghost, to prove the users are human. Interestingly, Lance Whitney of CNET, reporting the new tool, praised it as " a step in the right direction" but also asked, "But how long will it take an enterprising hacker to find a way past this latest security measure?"
The answer is not long. Steven Hickson, a graduate research assistant at Georgia Institute of Technology, with research interests that include computer vision and security, promptly put the strength of the tool to his test. He noted that "it is such an easy problem for a computer to solve."
Taking to his computer vision blog on Wednesday, he said, "The problem with this is that the Snapchat ghost is very particular. You could even call it a template. For those of you familiar with template matching (what they are asking you to do to verify your humanity), it is one of the easier tasks in computer vision."
He was able to defeat the system in less than an hour. He wrote up code such that a computer was able to circumvent the verification safeguard. Explaining the feat, Hickson said that "with very little effort" his code found the ghost. He found that troubling—that it required such little effort to do so.
"I'm not saying it is perfect, far from it. I'm just saying that if it takes someone less than an hour to train a computer to break an example of your human verification system, you are doing something wrong. There are a ton of ways to do this using computer vision, all of them quick and effective. It's a numbers game with computers."
Snapchat has taken security measures following the earlier data breach when account information was exposed. Snapchat said in early January that "We acknowledged in a blog post last Friday that it was possible for an attacker to use the functionality of Find Friends to upload a large number of random phone numbers and match them with Snapchat usernames. On New Years [sic] Eve, an attacker released a database of partially redacted phone numbers and usernames. No other information, including Snaps, was leaked or accessed in these attacks."Snapchat went on to say that "We will be releasing an updated version of the Snapchat application that will allow Snapchatters to opt out of appearing in Find Friends after they have verified their phone number. We're also improving rate limiting and other restrictions to address future attempts to abuse our service."
According to The Washington Post on Thursday, Mary Ritti, a company spokeswoman, said, "We continue to make significant progress in our efforts to secure Snapchat."
More information: stevenhickson.blogspot.com/201 … le-verification.html
© 2014 Phys.org