Fujitsu develops technology capable of searching encrypted data to maintain privacy
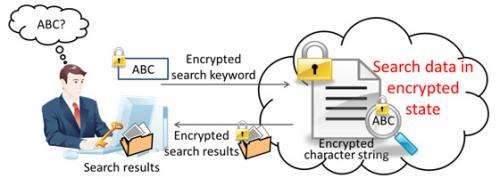
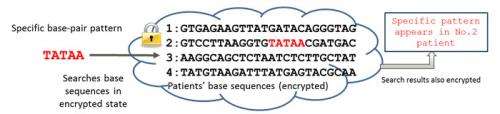
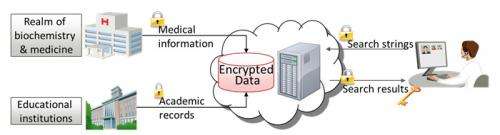
Fujitsu Laboratories today announced the development of a technology that can perform concealed searches of encrypted data in its encrypted form. Searching data while it is encrypted makes it possible to maintain a high level of privacy with no risk of leaks – particularly important for personal data such as DNA, medical data, biological data, and educational records. Through outsourcing, searches of confidential data can be carried out safely as text data and keyword search terms kept private. Whether or not search hits are obtained also remains undisclosed.
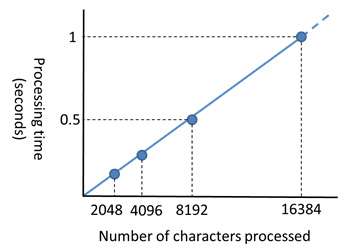
Based on homomorphic encryption which allows computations to be performed on confidential encrypted data without disclosure, Fujitsu has developed a new batch search method that accelerates the processing speed of searching for matches on the encrypted data. The new technology can search 16,000 characters in one second, and does not need an index of searchable keywords to be generated in advance. Instead, it makes discretionary searches of the encrypted text directly for any search key.
Details of this technology are being presented at the Fujitsu North America Technology Forum 2014, opening January 22 in Mountain View, California, and also at the Symposium on Cryptography and Information Security (SCIS2014), opening January 21 in Kagoshima, Japan.
With advances in cloud-based data storage and big-data analysis, information services for individual customers, such as healthcare administration, are appearing, however issues of peoples' private data being disclosed have been increasing. Fujitsu Laboratories has been working on technologies that enable more effective utilization of information while protecting privacy at the same time.
While there are encryption technologies, such as homomorphic encryption, that make it possible to perform calculations on data in an encrypted state, in order for data in the cloud to be useful, statistical calculations alone are not enough. For the data to be truly useful, technology that enables the data to be searchable has been needed (Figure 1).
Technological Issues
There are already a number of methods for searching data in an encrypted state, but these rely on pre-registering searchable keywords, and do not allow for freeform searching. These searches face certain implementation problems as well. As search results are unencrypted, this creates the potential for unwanted disclosure on the search engine. In addition, the search process is time-consuming.
About the Technology
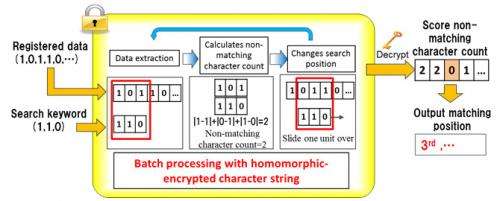
Fujitsu Laboratories has developed a technology that can search encrypted character strings in their encrypted state. This method is based on homomorphic encryption, which makes it possible to perform statistical calculations on encrypted character strings, but takes that approach a step further by performing multiple encrypted calculations in a single process, working in batch mode to determine whether the search key appears in the character string being searched. Because of the nature of homomorphic encryption, searchable keywords do not need to be registered in advance, so the data remains secret throughout the search process, which can cover 16,000 characters per second. Features of this technology are as follows.
1. Searches encrypted character strings directly for matches, eliminating need to pre-register keywords
Fujitsu Laboratories has developed a technology that matches encrypted text using an extension to the private calculation functions in homomorphic encryption. Because the process of finding matches between the search key and the encrypted character string is carried out while the character string is encrypted, there is no need for searchable keywords to be registered in advance. Also, the use of homomorphic encryption means that the entire search process is carried out using encrypted character strings. Even the search results are encrypted, so that they can only be read by someone with the decryption key, further heightening security.
2. Batch-mode calculations accelerate search process
Past search methods could only search for character strings one string at a time. Fujitsu Laboratories has developed a way to search the entire character strings in batch mode, resulting in dramatically faster processing (Figure 2). This method makes it possible to search 16,000 characters of character strings in one second or less (Figure 3).
Provided by Fujitsu

















