September 5, 2013 report
Researchers at Toshiba design quantum network for secure communications
(Phys.org) —A team of researchers at Toshiba Corporation has developed technology that allows up to 64 users to participate in a quantum key distribution (QKD) network with another single user. In their paper published in the journal Nature, the team describes how they built their network and how it might be used.
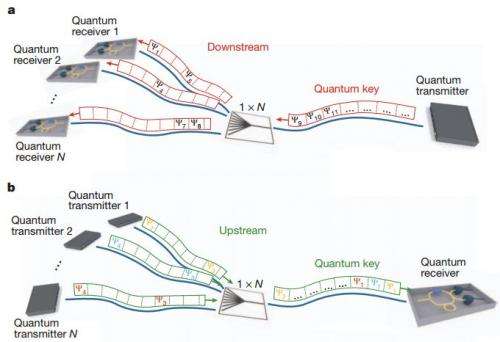
Scientists have known for years that conventional encryption schemes would become vulnerable as computers grew bigger, faster and more powerful. For that reason, researchers in the field have turned to QKD schemes because the laws of physics say that it's impossible for such keys to be used without them being disturbed in the process. That would make them the perfect encryption scheme. Unfortunately, to date, virtually all such systems that have been built are point-to-point and only work in straight line topographies. In this new effort, the researchers at Toshiba describe a way to allow a single transmitter to send quantum keys to 64 end users—in essence, creating a quantum key based network.
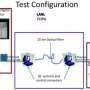
Quantum keys are based on polarized photons—by stringing them together in a series. But because they are photon based, they are extremely sensitive to noise. For this reason, communication systems that use them allow just a single node to communicate directly with just one other node—using very expensive transmitters and receivers on both ends. Making things even more difficult is that the lines that carry the data have to travel in a straight line. These two constraints have severely limited the ways in which the technology can be used. To date, other attempts to use quantum keys in a network have been mesh based, which means every node still only is able to send a key to one other single other node and vice-versa. To get around this problem the engineers at Toshiba built a hub device (with an expensive receiver) that could be shared by as many as 64 other people, allowing all 64 to send and receive encryption keys with one other node outside of the hub. They achieved this feat by employing two types of quantum transmitters that are able to operate at variable repetition rates along with stabilization components.
The researchers report that their approach is scalable and is constrained only by the power and speed of the transmitters and receivers. Thus it's conceivable that their approach could eventually be applied to much larger networks leading to widespread use of QKD in a variety of applications.
More information: A quantum access network, Nature 501, 69–72 (05 September 2013) DOI: 10.1038/nature12493
Abstract
The theoretically proven security of quantum key distribution (QKD) could revolutionize the way in which information exchange is protected in the future1, 2. Several field tests of QKD have proven it to be a reliable technology for cryptographic key exchange and have demonstrated nodal networks of point-to-point links3, 4, 5. However, until now no convincing answer has been given to the question of how to extend the scope of QKD beyond niche applications in dedicated high security networks. Here we introduce and experimentally demonstrate the concept of a 'quantum access network': based on simple and cost-effective telecommunication technologies, the scheme can greatly expand the number of users in quantum networks and therefore vastly broaden their appeal. We show that a high-speed single-photon detector positioned at a network node can be shared between up to 64 users for exchanging secret keys with the node, thereby significantly reducing the hardware requirements for each user added to the network. This point-to-multipoint architecture removes one of the main obstacles restricting the widespread application of QKD. It presents a viable method for realizing multi-user QKD networks with efficient use of resources, and brings QKD closer to becoming a widespread technology.
Journal information: Nature
© 2013 Phys.org