'Temporal cloaking' could bring more secure optical communications
(Phys.org) —Researchers have demonstrated a method for "temporal cloaking" of optical communications, representing a potential tool to thwart would-be eavesdroppers and improve security for telecommunications.
"More work has to be done before this approach finds practical application, but it does use technology that could integrate smoothly into the existing telecommunications infrastructure," said Purdue University graduate student Joseph Lukens, working with Andrew Weiner, the Scifres Family Distinguished Professor of Electrical and Computer Engineering.
Other researchers in 2012 invented temporal cloaking, but it cloaked only a tiny fraction - about a 10,000th of a percent - of the time available for sending data in optical communications. Now the Purdue researchers have increased that to about 46 percent, potentially making the concept practical for commercial applications.
While the previous research in temporal cloaking required the use of a complex, ultrafast-pulsing "femtosecond" laser, the Purdue researchers achieved the feat using off-the-shelf equipment commonly found in commercial optical communications.
Findings are detailed in a research paper appearing in the advance online publication of the journal Nature on June 5. The paper was authored by Lukens, senior research scientist Daniel E. Leaird and Weiner.
The technique works by manipulating the phase, or timing, of light pulses. The propagation of light can be likened to waves in the ocean. If one wave is going up and interacts with another wave that's going down, they cancel each other and the light has zero intensity. The phase determines the level of interference between these waves.
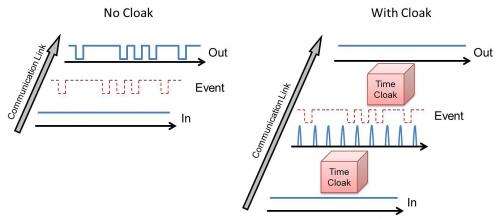
"By letting them interfere with each other you are able to make them add up to a one or a zero," Lukens said. "The zero is a hole where there is nothing."
Any data in regions where the signal is zero would be cloaked.
Controlling phase allows the transmission of signals in ones and zeros to send data over optical fibers. A critical piece of hardware is a component called a phase modulator, which is commonly found in optical communications to modify signals.
In temporal cloaking, two phase modulators are used to first create the holes and two more to cover them up, making it look as though nothing was done to the signal.
"It's a potentially higher level of security because it doesn't even look like you are communicating," Lukens said. "Eavesdroppers won't realize the signal is cloaked because it looks like no signal is being sent."
Such a technology also could find uses in the military, homeland security or law enforcement.
"It might be used to prevent communication between people, to corrupt their communication links without them knowing," he said. "And you can turn it on and off, so if they suspected something strange was going on you could return it to normal communication."
The technique could be improved to increase its operational bandwidth and the percentage of cloaking beyond 46 percent, he said.
The technology is reminiscent of recent advances in cloaking using new "metamaterials," assemblies that contain features, patterns or elements such as tiny antennas or alternating layers of oxides that enable an unprecedented control of light and that could make possible a cloak of invisibility. The temporal cloaking, however, does not require metamaterials, just commercially available phase modulators and optical fibers. The effect is called temporal cloaking because it hides data being transmitted over time, as opposed to "spatial" cloaking to hide physical objects.
More information: A temporal cloak at telecommunication data rate, Nature, 2013. www.nature.com/nature/journal/ … ull/nature12224.html
ABSTRACT
Through advances in metamaterials - artificially engineered media with exotic properties, including negative refractive index - the once fanciful invisibility cloak has now assumed a prominent place in scientific research. By extending these concepts to the temporal domain, investigators have recently described a cloak which hides events in time by creating a temporal gap in a probe beam that is subsequently closed up; any interaction which takes place during this hole in time is not detected. However, these results are limited to isolated events that fill a tiny portion of the temporal period, giving a fractional cloaking window of only about 10-4 percent at a repetition rate of 41 kilohertz - which is much too low for applications such as optical communications. Here, we demonstrate another technique for temporal cloaking, which operates at telecommunication data rates and, by exploiting temporal self-imaging through the Talbot effect, hides optical data from a receiver. We succeed in cloaking 46 percent of the entire time axis and conceal pseudorandom digital data at a rate of 12.7 gigabits per second. This potential to cloak real-world messages introduces temporal cloaking into the sphere of practical application, with immediate ramifications in secure communications.
Journal information: Nature
Provided by Purdue University